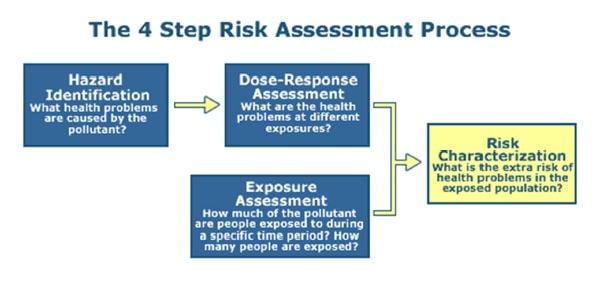
Source: United States Environmental Protection Agency (EPA)
A dose-response or concentration-response (probability) relationship describes how the frequency and severity of adverse health effects (the responses) are related to the amount and condition of exposure to an agent (the dose provided) (The National Institutes of Health, 2003).
A two-step process
- Step 1: Take an assessment of all data that is available or can be gathered through experiments. This is to document the dose-response relationship(s) over the range of observed doses (i.e., the doses that are reported in the data collected).
- Step 2: This consists of extrapolation to estimate the risk (probably of adverse effect) beyond the lower range of available observed data. This helps infer the critical region where the dose level begins to cause the adverse effect in the human population.
Two types of risk assessments
- Non-linear dose-response assessment
RfD = NOAEL (or LOAEL or BMDL)/UFs
The reference dose (RfD), No-Observed-Adverse-Effect Level (NOAEL), lowest-observed-adverse-effect level (LOAEL), Benchmark Dose Lower-confidence Limit (BMDL), uncertainty factors (UFs).
- Linear dose-response assessment
The cancer risk is determined by use of the following equation: Cancer Risk = Exposure x Slope Factor
Total cancer risk is calculated by adding the individual cancer risks for each pollutant in each pathway of concern (i.e., inhalation, ingestion, and dermal absorption), then summing the risk for all pathways.
Three basic approaches for quantifying exposure
Each approach is based on different data and has different strengths and weaknesses.
The combination of approaches can greatly strengthen the credibility of an exposure risk assessment:
- Point of contact measurement: Measure, at the point of contact (the outer boundary of the body) both exposure concentration and time of contact, then integrating them.
- Scenario evaluation: Estimated by separately evaluating the exposure concentration and the time of contact, and then combining them.
- Reconstruction: Estimated from dose, which in turn can be reconstructed through internal indicators (e.g. biomarkers, body burden, excretion levels) after the exposure has taken place.
Environmental Risk Assessments (ERA)
This is similar to a health risk assessment, in line with frequency, severity and exposure risk assessment methodology. ERA examines the effects of an entity or agent on humans (health risk assessment) and ecosystems (ecological risk assessment). The steps and methods used in an ERA will differ, depending on the risks, receptors, and end-points investigated (Fairman, et al. 1999).
Environmental risk assessment of marine activities
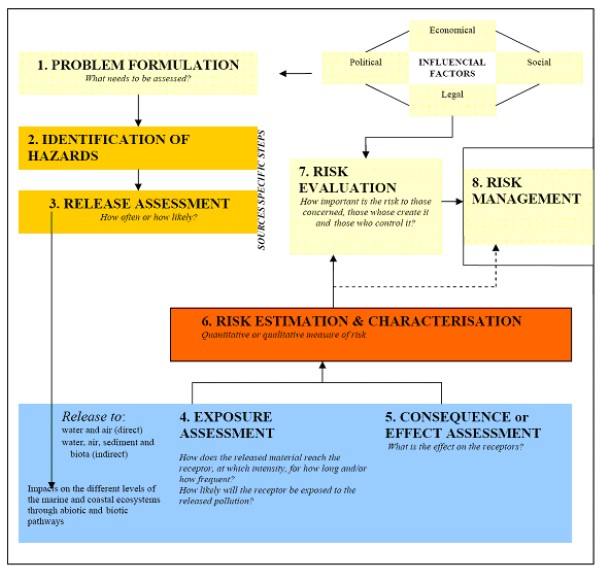
Source: Coastal Wiki
Natural disaster risk assessment (World Meteorological Organization, 1999)
An additional vulnerability variable is added to the frequency, severity and exposure methodology. The law enforcement sector combating money laundering and terrorist financing also use this approach per thematic area.
An example is flood risk assessment, which requires an intensive amount of data and can also be used to evaluate the net benefits of a proposed flood-mitigation programme.
Expected losses = hazard x exposure x vulnerability
- Estimation of the hazard: includes location, frequency and severity.
- Estimation of the exposure: includes the number of people, buildings, factories, and other elements at risk, exposed to the hazard.
- Estimation of the vulnerability of the elements at risk: usually expressed as percentage losses of people, buildings, crops, etc.
Disaster risk assessment (Thinda, 2009)
A serious disruption to the functioning of a community that causes widespread human, material, economic or environmental losses, which exceeds the ability of the affected community to cope with its own resources.
Disaster risk = H x V/C
H is Hazard, V is Vulnerability and C is Capacity to mitigate and respond to disaster events.
This method would add value to an OHS risk assessment by taking into account the vulnerability of workers, systems, processes and other organisational assets.
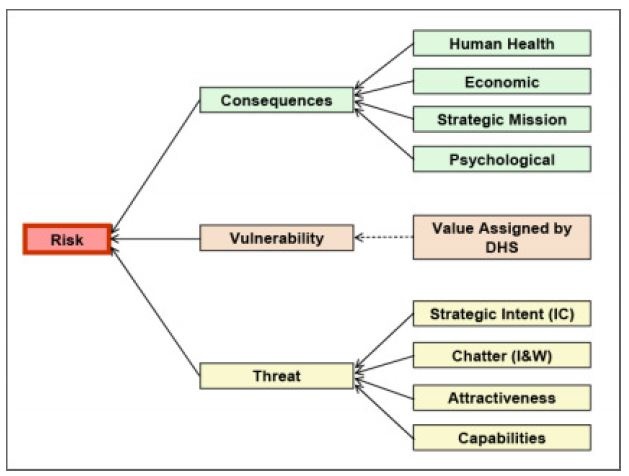
Terrorist attack risk assessment
The USA Department of Home Land Security uses an approach to allocate funds to state or local governments to enhance their ability to prepare for and respond to terrorist acts. This fund allocation requires an assessment of risk using a formula as follows:
R=T*V*C
Threat (T) to a target/area, vulnerability (V) of the target/area, consequence (C) of an attack on that target/area.
The assessment can be asset- or geography-based as illustrated in the charts below.
Asset-based risk analysis attributes
State geographic risk analysis attributes
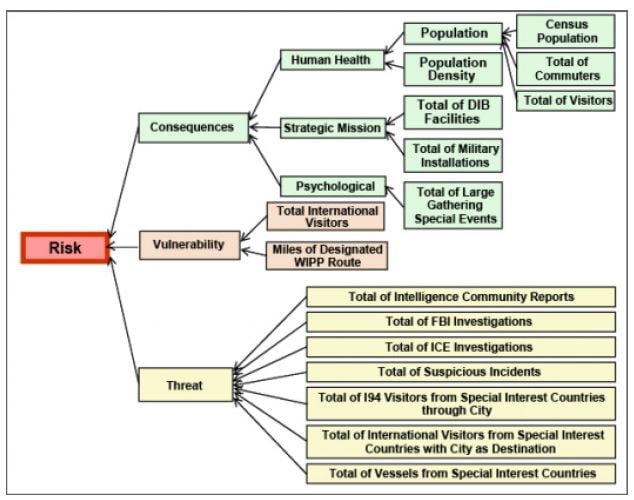
Source: Masse, O’Neil & Rollins, 2007
Terrorist attacks and other technical risk assessments, such as environmental health risk assessments, require technical and medical knowledge to assess frequency, severity, exposure, and vulnerability, which gives an indication of sophisticated matrix-based methods by unpacking the risk value components into their contributing factors to analyse and evaluate risks.
Other types of risk assessment
- Sensitivity analysis
- Force field analysis
- Pareto analysis, also known as A-B-C analysis (qualitative)
- The Microsoft Corporate Security Group Risk Management Framework
- Preliminary Risk Analysis
- Root causes analysis techniques, e.g. 5-Whys
- Human Reliability Analysis (HRA) - a special form of Fault tree and event tree analysis
- Structured What-If (SWIFT) Analysis
- Event and Causal Factor Charting
- Hazard Analysis and Critical Control Points (HACCP) – food safety
- Critical control point – mining
- Environmental risk and impact assessment
- Change Analysis (ChA)
- Pareto Analysis (PA)
- Bayesian analysis
- Resilience engineering Hollnagel, et al. (2006).
- FRAM and STAMP (Hollnagel, 2004; Leveson, 2004, 2011)
- Human reliability analysis
- Reliability centred maintenance
- Layer protection analysis (LOPA)
- Sneak circuit analysis
- Markov analysis
- Multi-criteria decision analysis (MCDA).
- The triplet (C’, Q, K): a possibility and evidence theory based method, which is an alternative qualitative form of the matrix approach due to the weak background knowledge to estimate probability. C’ is some specified consequences, Q a measure of uncertainty associated with C’ (typically probability) and K is the background knowledge that supports C’ and Q (which includes a judgement of the strength of this knowledge) (Aven, 2016).
- Electrical system simulation
- Benchmarking methods
- NIST SP 800-30
- OCTAVE
- FAIR
- TARA
- ISACAs COBIT 5
- Cost analysis techniques (more technical as use more sophisticated mathematical formulae)
- Simple screening and choice methods
- Abatement cost function analysis
- Financial analysis
- Cost-Benefit Analysis
- Cost-Effectiveness Analysis
- Input-Output Models
- General Equilibrium Models
- Multi-Criteria Analysis
- Others
- Reaction Matrix
- Action Error Analysis
- Work/job Safety Analysis
- Management Oversight and Risk Tree
- Consequence Analysis
- Cause-Consequence Analysis
- Energy Barrier Analysis
- Clustering risk assessment
- Engineering approach to risk assessment of process improvement
- Work-machine system risk assessment on three levels using operating hazard analysis, preliminary hazard analysis and HAZOP
- Safety of machinery ISO 13849:2015 Safety-related parts of control systems – Part 1: General principles for design
- ISO 12100: 2010, Safety of machinery – General principles for design – Risk assessment and risk reduction
Future Research Directions (Aven, 2016)
The concept of emerging risk has gained increasing attention in recent years. Flage and Aven (2015) performed an in-depth analysis on the emerging risk concept, and in particular its relation to black swan type of events through the known/unknown. Some emerging risks relate to an activity when the background knowledge is weak but contain indications or justified beliefs that a new type of event would occur in the future and potentially have severe consequences on something humans value. The weak background knowledge makes the specification of scenarios difficult (consequences and the event itself) (Flage & Aven, 2015).
Further development in risk assessment techniques is expected to address the challenges linked to the knowledge dimension and the time dynamics. There is a need to balance different risk management strategies in an adaptive manner, including cautionary strategies and attention to signals and warnings. There is also a need for research and development (R&D) to obtain adequate modelling and analysis methods to handle the different types of systems. Examples include critical infrastructures, such as electrical grids and transportation networks, which are complex systems and are often interdependent. There is potential for significant improvement in the way security is assessed by developing frameworks that integrate the standard security approaches and the ways of assessing and treating uncertainty. The paper by Aven (2013) provides an example of work in this direction.
Societal risk decision-making become a challenge, which is characterised by many, diverse stakeholders. Some of the challenges and research issues relate to the following aspects (Aven & Zio, 2014; SRA, 2015):
- How the outcomes of the risk and uncertainties assessment should be best described, visualised and communicated, for their informative use in the process of societal decision-making involving multiple and diverse stakeholders.
- How the issues of risk acceptability should be seen in relation to the measurement tools used to make judgements on risk acceptability, which represents the value generating processes at the societal level.
- How the managerial review and judgement should be defined in this context.




