
Today we drill even further down into the different types of risk analysis and their efficacy, taking a look at:
- The top 10 business risks ranked by interviewees
- Risk summary by year
- Bowtie analysis
- FMEA or FMECA
- Business impact analysis
- NIST SP 800-30 (a qualitative matrix approach)
- CRAMM (Qualitative)
Top 10 business risks ranked by interviewees
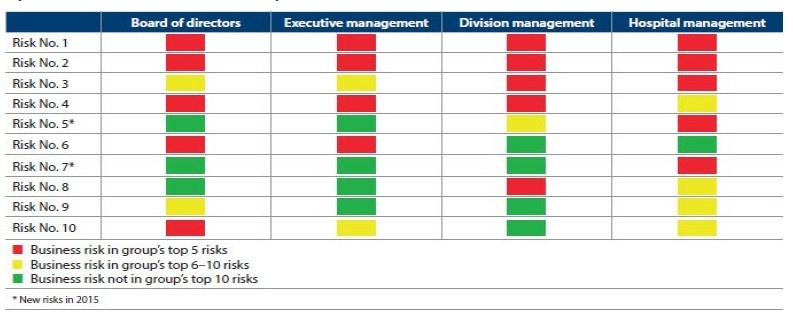
The chart below is an example of a summary report. Because all risks are not equal, the company prioritises them by assigning points to each respondent's risk ranking:
- 5 points for the top risk
- 3 for the second, and
- 2 for the third.
Risk summary by year
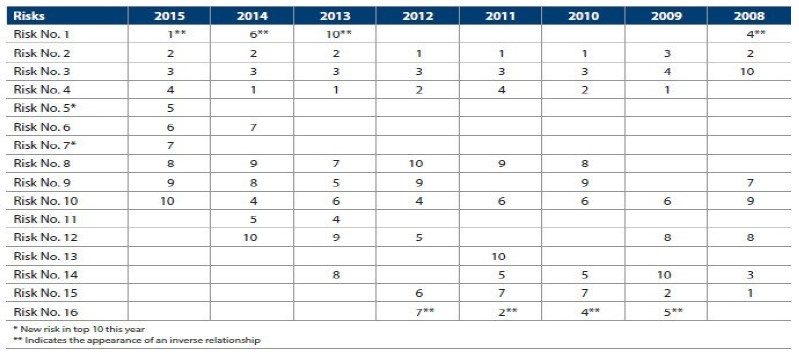
Source: Amato, 2017
The goal is to obtain from these experts an evaluation of the probability and cost of incidents in scenarios. This approach is an alternative to when historical data is not sufficient to implement a purely statistical method. According to Fimarkets, It is especially useful to assess the impact of severe risk events, or the impact of simultaneous events.
Bowtie analysis
Bowtie is a combination of fault-tree analysis (causal factors to identify undesired events) and event-tree analysis (systems to mitigate consequences) in a simplified two scenarios for identifying multiple root causes, and prevention and mitigation strategies. While fault trees are based on mathematical modelling, event trees have no inherent mathematical value. The combined tools help to identify the most critical controls (Australian Government, 2016).
The bowtie analysis method for identifying critical risk control measures
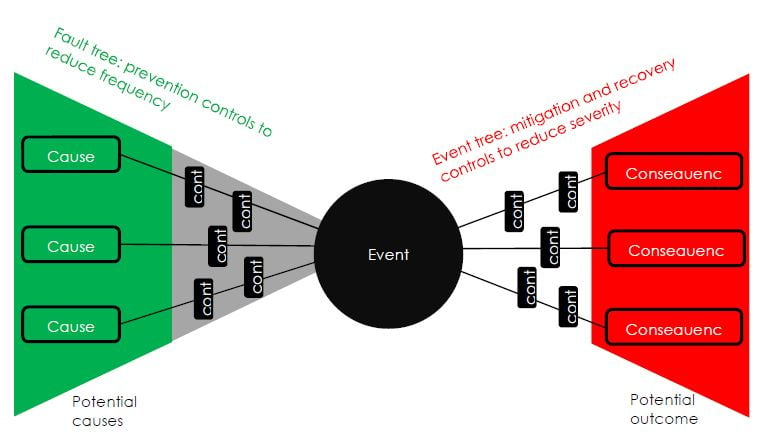
Source: Joy, 2015
Assurance of controls can be a part of the bowtie analysis, as illustrated in the chart below. Although it is not exactly a risk evaluation, control assurance can affect the evaluation process by highlighting those opportunities that are most likely to be successful.
Advanced bowtie with control erosion factors and assurance
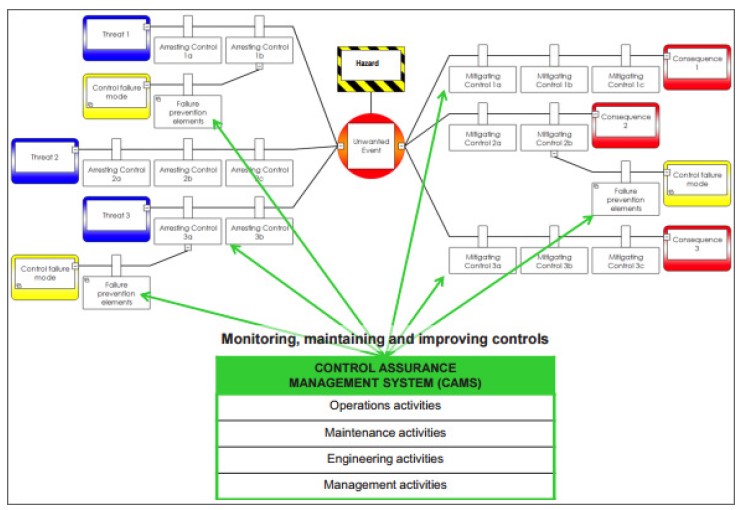
Source: Australian government, 2016
- FMEA or FMECA (Rot, 2008): FMEA (Failure Mode and Effects Analysis) and FMECA
(Failure Mode and Effects Criticality Analysis) methods were developed in the 1950s for analysing the reliability of weaponry. The method is still used in the aircraft, space and electronic industries today. The essence of FMEA/FMECA is the analysis of impact of every potential defect on the functionality of the whole system, and the order of potential defects according to the level of its severity. Additionally, the FMECA method introduces the analysis of the degree of defect severity, and examines whether it has critical character for functionality of the whole evaluated system (Rot, 2008). These methods are quite laborious, require knowledge and experience of persons who apply them; they are supported with specialist tools, using the elements of knowledge engineering and fuzzy logic.
As part of FMEA, a risk score and risk prioritisation number (RPN) are assigned to the deviation or to the stage of the process that is affected, which helps categorise the deviation.
RPN = Probability x Severity x Detection
Typically, if the RPN falls within a pre-determined range, corrective action may be recommended or required to reduce the risk (i.e. to reduce the probability of occurrence, increase the probability of prior detection or, if possible, reduce the severity of the failure effect). It provides an indication of the effectiveness of corrective actions and can also be used to evaluate the value to the organisation, using the % reduction in RPN:
% reduction in RPN = (RPNinitial-RPNrevised)/RPNinitial
Item RPN might be useful as a way to compare components and determine priority for corrective action or to determine which component will be selected for inclusion in the design.
RPNitem= RPNcause1+…+RPNcausen
(Bhattacharya, 2015)
- Business impact analysis
Evaluate the threats facing the organisation and their consequences
Such analysis may start with a worst-case scenario, focusing on the business process that is most critical to recover and how it might be recovered remotely. The business-impact analysis should identify critical business functions and assign a level of importance to each function based on the potential operational or financial consequences. It should also set recovery-time objectives and the resources required if an incident occurs (SCRLC, 2011).
- NIST SP 800-30 (a qualitative matrix approach) (Rot, 2008)
Example of matrix according to the NIST methodology
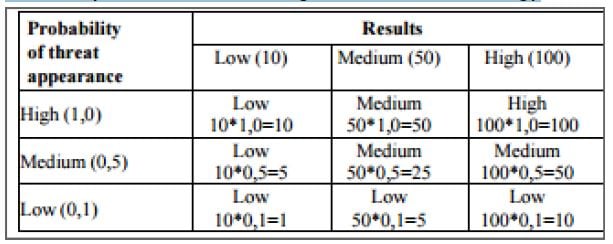
- CRAMM (Qualitative) (Rot, 2008)
CCTA’s Risk Analysis and Management Methodology (CRAMM), by the UK Government Central Computer and Telecommunications Agency (CCTA), is the governmental standard of analysis and risk management. The process of risk management according to this methodology consists of three subsequent stages:
- Identification and evaluation of resources
- Evaluation of threats and susceptibility
- The selection and recommendation of protection mechanisms
The main aim of IT risk analysis is to:
- determine the probability of occurrence of incidents interfering with the correct functionality of resources
- generate lists of main threats that could concern a given asset group
- determine the risk level for each group in five degree scale.




